Email security issues plague every single business. Why? Because it’s an easy point of failure for scammers and hackers to exploit.
According to our 2025 IT Trends Report, 48% of SMBs experienced a security threat in the past year, with many incidents originating from email-based attacks. To mitigate these risks, SMBS should implement robust email security measures, such as encryption protocols and employee training programs focused on identifying and preventing phishing attempts.
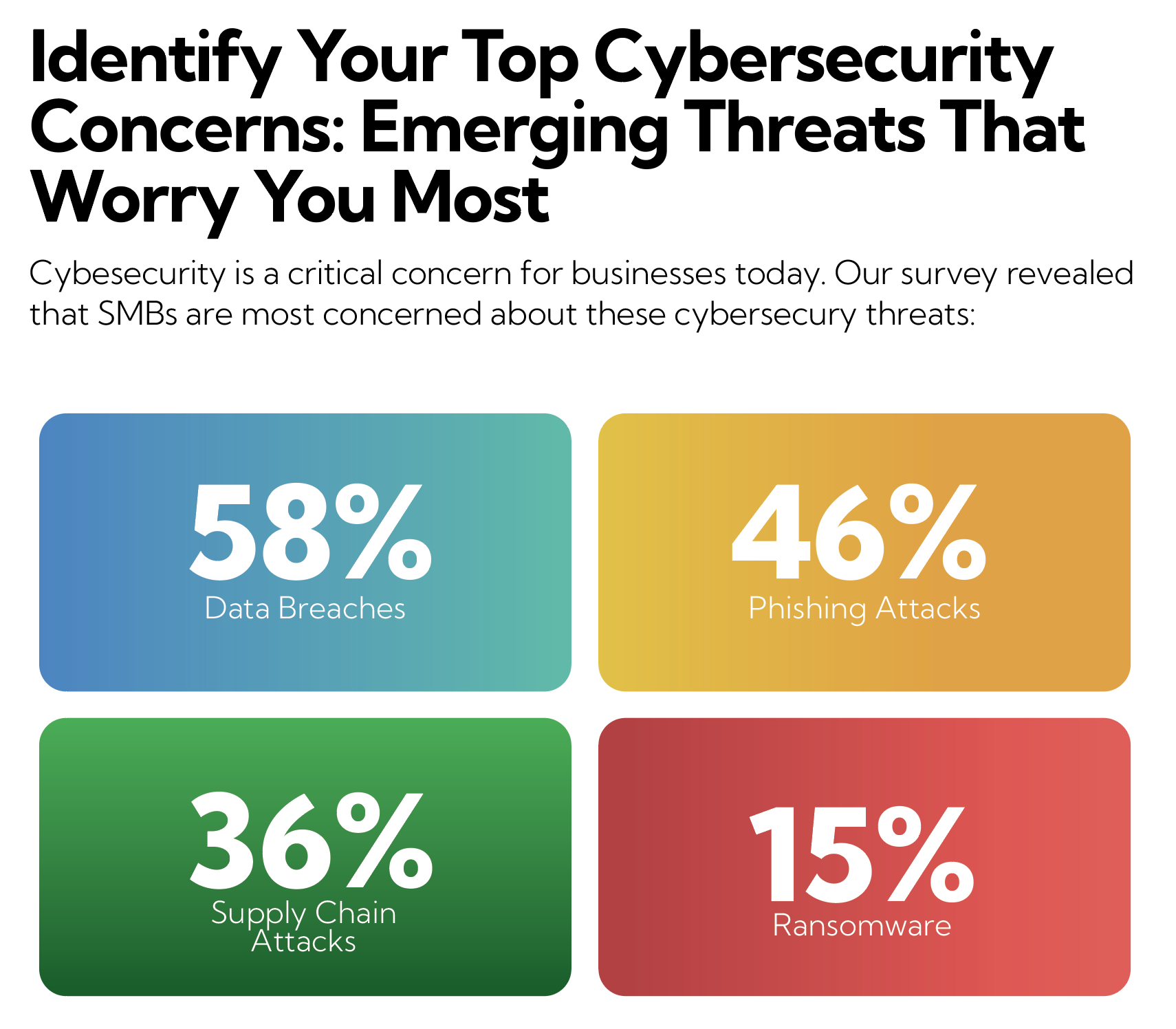
For more IT Trends and Insights, download our
2025 IT Trends Report for Small & Medium Businesses.
1. Sending Unencrypted Emails
Sending confidential data over email is a widespread practice in the business world, but it’s also one of the most significant security risks. If your emails aren’t properly encrypted, cybercriminals can easily intercept and read them, leaving your sensitive information vulnerable to theft or misuse.
To reduce this risk, it’s important to have a clear policy about what should and shouldn’t be sent over email. For example, if sensitive data can be shared through a secure file transfer service or a virtual private network (VPN), then it’s advisable to use those methods instead of email.
To reduce this risk, it’s important to have a clear policy about what should and shouldn’t be sent over email. For example, if sensitive data can be shared through a secure file transfer service or a virtual private network (VPN), then it’s advisable to use those methods instead of email.
2. Malware
Malware is a broad term used to describe various types of malicious software designed to harm your computer or steal your data. Here are some of the most common types of malware that can infect your computer through email:
- Viruses: These are the most commonly known types of malware that can replicate themselves and infect other files on your computer.
- Trojans: These are malware that disguise themselves as harmless software but can cause damage to your computer once executed.
- Ransomware: This is a type of malware that encrypts your files and demands a ransom payment to restore access.
- Spyware: This is malware that secretly monitors your computer activity, tracks your internet usage, and steals sensitive information.
- Adware: This type of malware displays unwanted advertisements and pop-ups on your computer.
We see businesses scrambling to recover after malware attacks all the time. Malware sneaks in and wreaks havoc before anyone realizes anything’s wrong. Where does malware love to hide? Emails. Why? It’s easy to make an email seem legitimate, such as sending a malicious attachment but, making it seem as if it came from a co-worker.
Unless employees check the sender’s address or double-check with co-workers to ensure the email is from them, they open the malware-infected attachment, and the damage is done.
To prevent malware and viruses from infecting your network, ensure your business has robust antivirus software installed on all devices. Regularly scan for malware and viruses and enforce strict email attachment policies.
3. Phishing
90% of security breaches in companies are a result of phishing attacks, and with small and mid-size businesses averaging $1.6 million in recovery costs, phishing is easily one of the biggest email security risks.
Phishing happens when attackers impersonate legitimate senders, such as banks or other trusted sources, and lure recipients into clicking on malicious links or downloading infected attachments. This can lead to sensitive information being compromised or malware being installed on your network.
We’ve seen many instances where employees unknowingly handed over their credentials to hackers, who then used those credentials to compromise a business’s network. A link or attachment can easily appear legitimate, but in reality, it’s designed to steal their data.
4. Email Spoofing
Email spoofing is a type of cyber attack where a hacker sends an email that appears to be from a legitimate source, but in reality, it’s been forged. This can be done to trick the recipient into disclosing sensitive information, downloading malware, or wiring money to a fraudulent account.
To protect against email spoofing, businesses can implement several measures. One of the most effective is to use email authentication protocols like SPF, DKIM, and DMARC. These protocols verify that an email message is from a legitimate sender and has not been tampered with in transit.
Businesses should also encourage their employees to be cautious when opening emails and to scrutinize sender information and message content carefully. If an email looks suspicious, employees should be trained to report it to the IT department or security team.
5. Email Bombing
Email bombing is a type of cyber attack where attackers flood an email inbox with a large number of emails, overwhelming the system and causing it to crash. This can result in lost productivity and even cause permanent damage to your IT infrastructure.
Email bombing attacks can target any business, but they are especially effective against businesses that rely heavily on email for communication or customer support. Some examples of businesses that may be susceptible to email bombing include:
- Customer service and support centers that receive high volumes of email inquiries
- E-commerce businesses that send frequent promotional emails to customers
- Financial institutions that use email to communicate with customers about sensitive account information
- Healthcare organizations that use email to communicate with patients and share medical records
- Government agencies that use email for public outreach and communication.
To prevent email bombing, ensure that your email server is configured to limit the number of emails that can be received within a certain time period. Additionally, you can use filters to automatically delete suspicious emails.
6. Weak Passwords
No matter how strong a business’s network is, a weak email password still poses a threat. Employees who use easy-to-guess passwords, reuse passwords across multiple accounts, or fail to change their passwords regularly can put their organization at risk.
To improve password security, businesses can implement multi-factor authentication (MFA). MFA requires users to provide multiple forms of identification, such as a password and a code sent to their phone or email, before they can log in.
Safeguard Your Business With Cybersecurity Measures
Email security is an essential aspect of safeguarding your business’s sensitive information. By understanding the most common email security issues and implementing robust security protocols, you can protect your organization from cyber threats and ensure that your communication remains secure.
At our ISOutsource, we specialize in providing expert email security solutions to businesses of all sizes. Whether you need help with email encryption, spam filtering, employee training, or any other aspect of email security, we are here to help.
Don’t wait until it’s too late to protect your organization’s email systems. Contact us today for an IT consultation to learn more about how we can help you improve your email security posture and keep your business safe from cyber threats.
