90% of businesses now have at least 26% of their workforce operating remotely, yet many still struggle with IT challenges like device management (41%), connectivity issues (41%), security risks (40%), and collaboration inefficiencies (39%).
According to our 2025 IT Trends Report, SMBs that fail to focus on remote work security and optimize their remote work infrastructure risk falling behind. To thrive in this evolving landscape, businesses must invest in cybersecurity, cloud solutions, and collaboration tools that support seamless remote operations while protecting sensitive data.
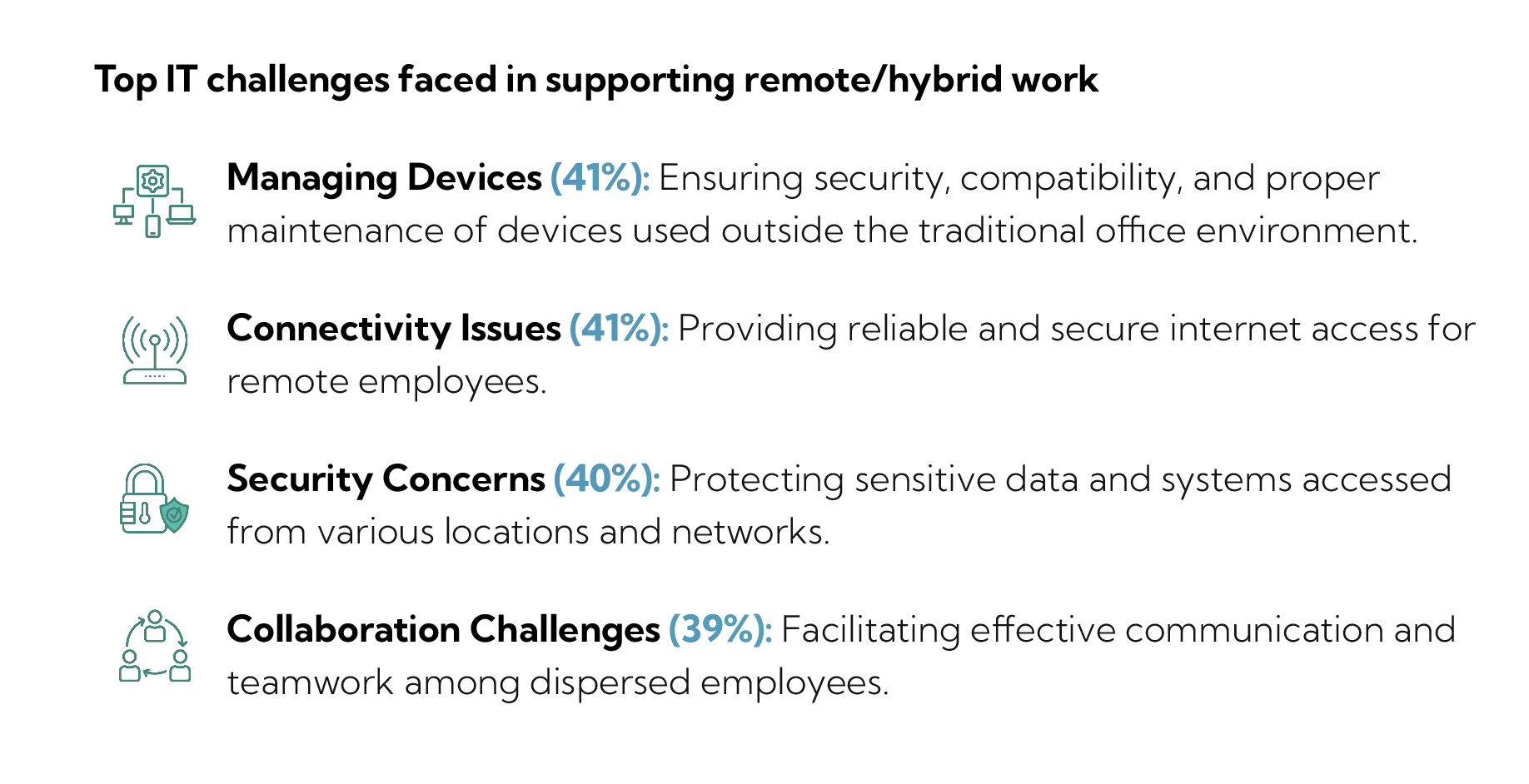
By addressing these IT challenges, SMBs can unlock the full potential of remote teams and drive long-term growth.
1. Use of Personal Computers & Mobile Devices
Over 50% of remote teams use a personal computer to do their work and just as many are using personal mobile devices. With an increase in bring-your-own-device (BYOD), the line between personal and business use on technology devices is more blurred than ever, and where lines are blurred, privacy concerns, exposure, and vulnerabilities grow.
One key way the use of personal computers and devices introduces risk to your business or organization:
- Unknown or no BYOD security policies in place.
Even if your company has elaborate policies around using personal computers and devices for work, if your teams are misinformed or unaware of the policies or how to comply with them, every device becomes a risk for security breach.
2. Patching & Maintenance Coordination
Regular patching and maintenance of systems, software, and devices used in your organization are key to reducing exposure to cybersecurity attacks. With teams and systems scattered in various environments, the coordination of the maintenance can become complicated without physical access to all endpoints, the diversity of operating systems, and a host of other potential complications when all users don’t operate in the same environment.
3. Unsecured Home Networks
In general, home WiFi networks are naturally more vulnerable to cybersecurity attacks due to their no or minimal security protection. Additionally, most home network users don’t account for the variety of connected devices that increase their risk. Teams working remotely should consider any device connected to their home network a risk to their personal cybersecurity as well as their company’s, highlighting the importance of remote work security.
4. Spotty Connectivity
Many businesses go to great lengths and spend significant amounts of money on software to prevent viruses from infecting devices utilized for work. So how does connectivity play a role? Many antivirus programs require connectivity to work at full capacity, and when connectivity fails, their effectiveness is diminished. 1 in 4 home WiFi networks have intermittent connectivity, creating opportunities for hackers to do their worst.
5. Passwords
The sharing, storing, and general practices around password creation and use are still a key vulnerability for people and businesses alike. Most businesses utilize secure password storage programs such as LastPass and Dashlane but even using these may not mitigate the risks completely. Why? Human error and lack of training around password protocols.
If your company is not utilizing secure and encrypted password storage and hasn’t trained your employees on best practices in password creation, sharing, and storage, you are at risk.
6. More IP Addresses
IP addresses serve as identifiers for devices utilizing any given network. Each IP address is an avenue for hackers to deploy any number of cybersecurity attacks, such as phishing, ransomware, spyware, DOS, or DDoS. The more addresses utilizing your systems and tools, the more inroads there are for those looking to do damage.
Over 58% of small and medium businesses are the target of cybersecurity attacks, and no industry is immune to these risks. If you don’t think it could happen to your small business, read our case study on how a small nonprofit organization fell victim to a ransomware attack.
Proactive IT and Technology Support is More Important Than Ever
Some businesses do not survive data loss or breach events and if they do, they may lose months or years of work. We hear about cybersecurity breaches and attempts from businesses every single day and due to changing work environments, flexibilities, and remote work security concerns, the risk is constantly increasing. Reactive support and bare minimum protocols not only leave you open to more risk but end up costing your business or organization more in the long run.
So don’t wait to get a security strategy in place. Reach out to our team to start the conversation.
